Web applications today require secure and scalable authentication mechanisms to protect user data. Two of the most popular authentication strategies are Session-based Authentication and JWT (JSON Web Token)-based Authentication. While both achieve the goal of identifying users, they work differently under the hood and suit different types of applications.
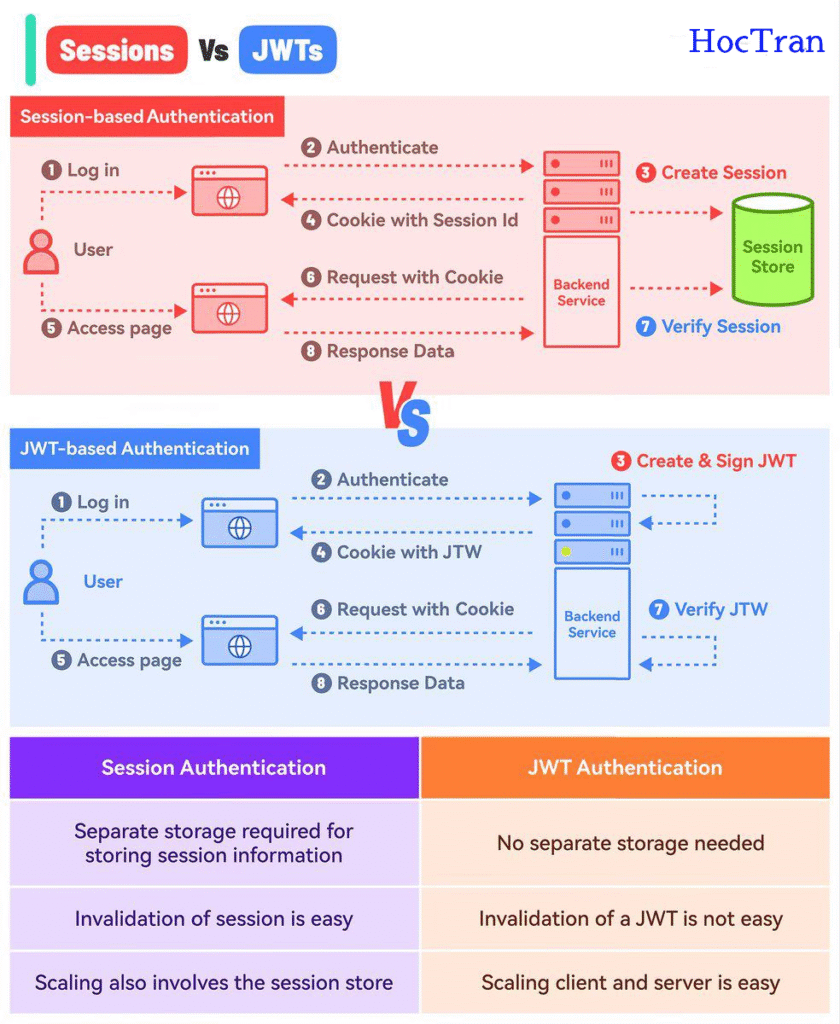
🔁 Session-based Authentication
How It Works
Session-based authentication follows a server-side stateful approach. Here’s the step-by-step flow:
- Login: The user enters credentials in a login form.
- Authenticate: The backend verifies the credentials.
- Create Session: On successful authentication, the server creates a session and stores it (usually in memory, Redis, or a database).
- Set Cookie: A cookie containing the
Session IDis sent to the user’s browser. - Access Page: The user accesses another page.
- Send Request: The browser sends the session ID in the cookie to the server.
- Verify Session: The server validates the session ID using the session store.
- Return Data: If valid, it returns the appropriate response.
Key Characteristics
- Requires a session store to keep track of logged-in users.
- Easy to invalidate sessions (e.g., on logout or timeout).
- Scaling across servers requires sticky sessions or centralized storage.
🔐 JWT-based Authentication
How It Works
JWT uses a stateless approach by embedding the session data directly in a digitally signed token. Here’s how it works:
- Login: The user logs in.
- Authenticate: Backend verifies credentials.
- Create & Sign JWT: A JWT is generated with user data and signed using a secret/private key.
- Set Cookie or Header: The JWT is returned and stored client-side (typically in cookies or
localStorage). - Access Page: The user navigates to another page.
- Send Request: The browser sends the JWT with the request (commonly via the
Authorizationheader). - Verify JWT: The server validates the signature and extracts the payload.
- Return Data: If valid, it sends back the requested data.
Key Characteristics
- No server-side storage of session data.
- JWT includes payload (e.g., user ID, expiration) and is self-contained.
- Can be used across domains and services (great for microservices).
- Difficult to invalidate tokens once issued (unless using blacklists or short expiration times).
🔍 Key Differences at a Glance
| Feature | Session Authentication | JWT Authentication |
|---|---|---|
| Storage | Server-side (e.g., in Redis or memory) | Client-side (e.g., in cookies or localStorage) |
| Session Invalidation | Easy (delete from store) | Difficult (must wait for expiry or use blacklist) |
| Scalability | Needs session replication or central store | Easier to scale (no session state on server) |
| Security Risk | Session hijacking if cookies aren’t secured | Token theft if stored insecurely or leaked |
| Ideal for | Monolithic applications | Distributed, stateless, and mobile-first apps |
🧠 When to Use What?
| Scenario | Recommended Strategy |
|---|---|
| Traditional web apps with login/logout | Session-based |
| RESTful APIs or SPAs | JWT-based |
| Need easy revocation | Session-based |
| Need scalability and stateless design | JWT-based |
⚠️ Security Considerations
- JWT:
- Always sign with strong secrets or private keys.
- Use short expiration times and rotate tokens frequently.
- Store securely in HttpOnly cookies to prevent XSS attacks.
- Sessions:
- Use secure cookies, enforce HTTPS, and regenerate session IDs.
- Monitor and clear stale sessions regularly.
🔚 Conclusion
Both JWTs and Sessions are powerful tools when used correctly. Sessions offer simplicity and better control for traditional applications, while JWTs shine in distributed, stateless environments. Understanding the trade-offs in security, scalability, and revocation helps you choose the right authentication strategy for your application.